Simple Overflow
This is a very simple crackme. The goal is to get “you are logged in as admin”. Patching is not allowed. The solution should contain an exact description, how this works. Have fun!
- Category: rev
- Challenge author: BitFriends
- Challenge link: crackmes.one
Solution:
1. Run the binary
$ ./a.out
enter password: test
uid: 1
you are logged in as user
The binary accept any strings and logged in as user, but our goal is to logged in as admin
2. Use IDA to view its assembly code
As the binary will have some check function to validate the admin input
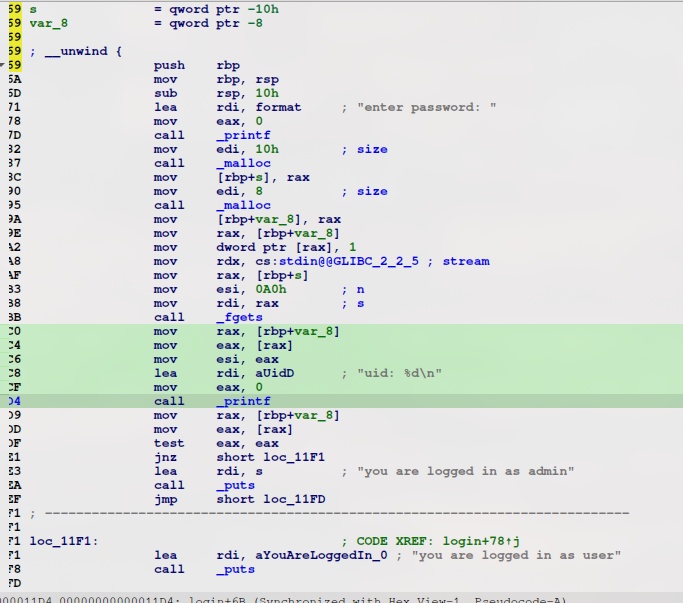
To summarize the operations:
sys_writeprints out the questionsys_readtakes input aspasswordwith the count of 16 bytes (0x10)_verifyiterates over the first four charaters by ASCII then add the result into r13 registers which will be compared with r15 registers_incorrectif the check is failed_correctif the check is correct
Dive deeper in the assembly:
test eax, eax
jnz short loc_11F1
lea rdi, s ; "you are logged in as admin"
We able to use debugger to manipulate the register value to jump to lea by fixing zero flag when breakpoint is set at test instruction.
3. Use GDB debugger
We can set breakpoint at login function and then set another breakpoints at *0x5555555551DF
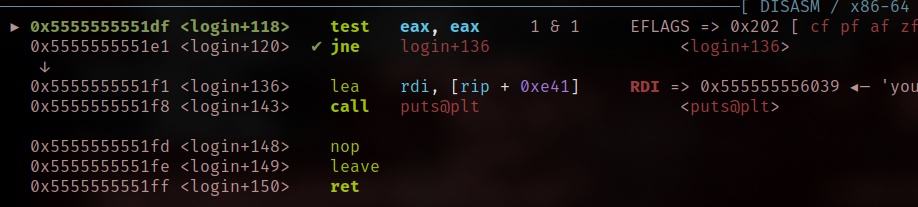
Next, modify the register value of eax to 0 and then continue
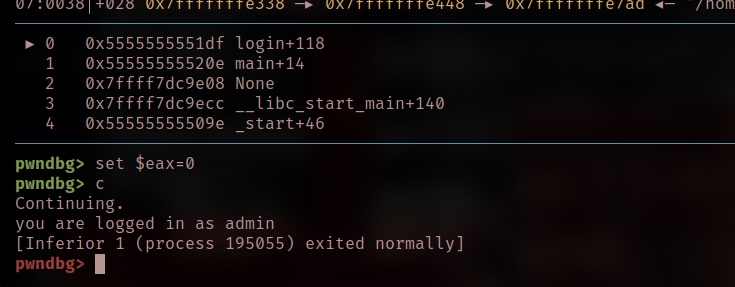
Now, we are login in as admin
.gdb_history:
b login
run
b *0x5555555551DF
c
set $eax=0
c